Today, the subject of computer network security has become paramount for businesses of all sizes. According to the Euler Hermes 2021 Barometer, identity theft accounts for 38% of cyberattacks on small and medium-sized businesses. In fact, two out of three companies suffer from this type of fraud every year.
That’s why it’s becoming essential to implement a digital code authentication system for account verification in your IT security strategy. In this article, we present the benefits of having such a system via SMS.

What is identity theft?
This type of fraud occurs when someone gets access to your personal data, confidential data of your company or your employees, and uses this information to make purchases, open a bank account, receive medical care, rent a property; in short, different actions carried out in your name but without your authorization.
How does identity theft happen?
Identity thieves can access your personal information in a variety of ways. Here are the most common examples.
Phishing
Cybercriminals send fraudulent e-mails that appear legitimate. By clicking on the links in the emails, the victim accidentally downloads malicious software (malware).
This software can compromise the user’s privacy, extract personal information from the victim’s computer and send it to cybercriminals.
Data breaches
A data breach puts the personal information and privacy of millions of people at risk. For example, the Equifax data breach exposed the personal information of as many as 147 million users.
Number for verification: what methods to protect yourself from identity theft?
It may seem obvious, but the most crucial measure to implement when securing your company’s data is the implementation of good internal controls.
It’s important to incorporate good practices when it comes to your employees’ passwords, or limiting their access to certain documents, such as customer lists or accounting files.
In addition to changing passwords at least once every three months, it is essential to use random password generators, perform external password backup, and implement two-factor authentication to improve your data security. For this type of verification, SMS is the ideal solution.
Number for verification: why use SMS?
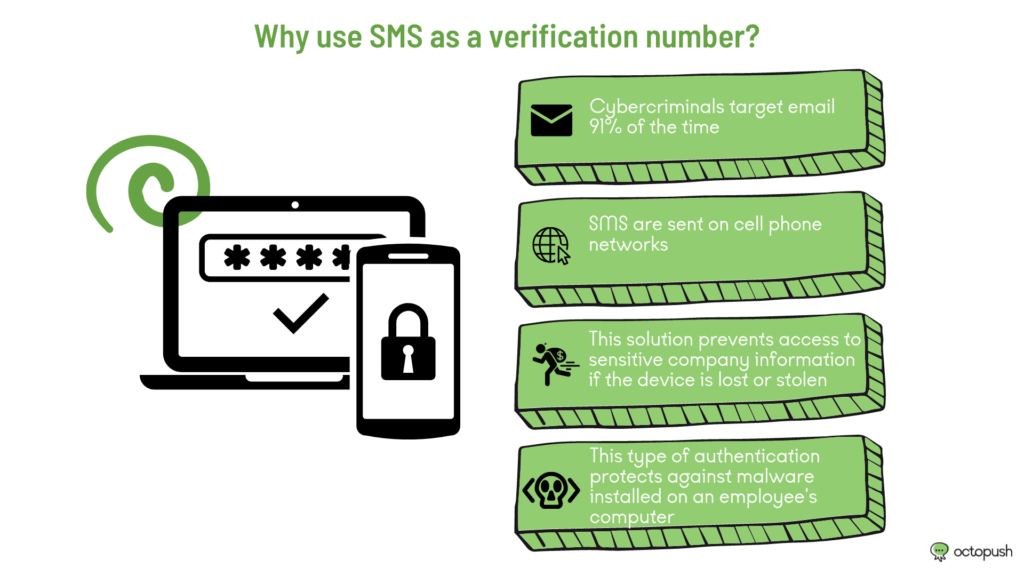
Why use SMS as a verification number?
Typically, applications and software use email to verify user identity. However, according to a survey by NDNM, cybercriminals target emails 91% of the time.
SMS messages are sent over cell phone networks, which means that successful identity theft requires cybercriminals to have access to the user’s computer and cell phone at the same time.
Telecommuting, as well as the trend of bringing one’s own device to work, presents additional risks to businesses. Devices should be password protected to prevent access to sensitive company information if the device is lost or stolen.
A two-step authentication process is necessary. If your company’s network security is compromised due to malware installed on an employee’s computer, for example, network access remains protected because the software does not have access to the verification code sent by SMS to the employee who owns the account.
Your data remains intact.
Number for verification: a solution for mobile wallets
Mobile payment solutions carry real security risks. This applies to both the companies offering this service and their users. Users need to protect their credentials. Because a fraudster can easily divert funds from legitimate transactions to another account. Especially if they have access to the account.
Companies offering mobile payment systems must assure their customers that they are using the best encryption methods. That is, solutions that require the highest level of authentication possible.
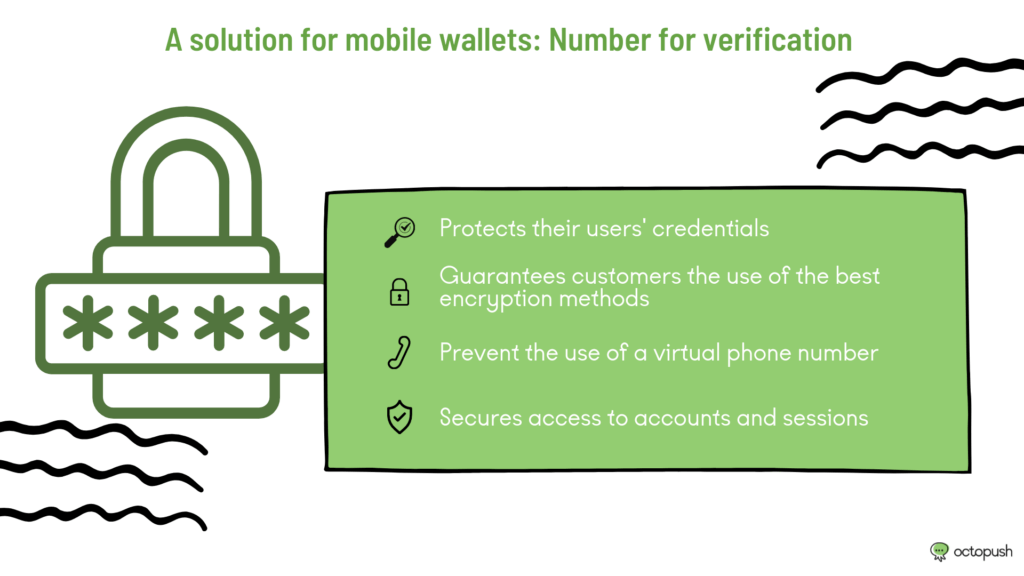
In this case, receiving an OTP key via SMS is not optional. Authentication must be mandatory to link the owner of the phone number to their account simply via an OTP message. Companies offering mobile payment must also prevent the use of a virtual phone number. A practice that circumvents verification. This is because it allows the creation and use of accounts without a fixed identity.
Finally, two-factor authentication is a method of securing access to accounts and sessions. Every company should implement it. This service sends your employees an SMS containing a code that allows them to access your company’s network.
